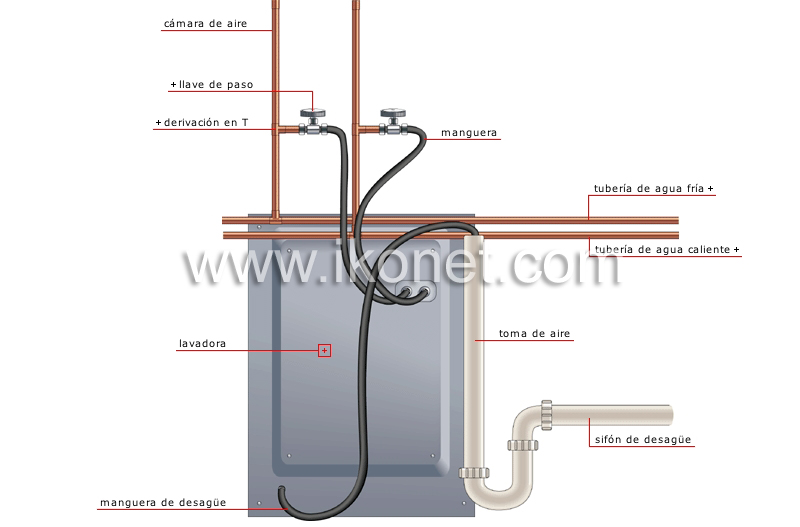
BricoLoco Kit Manguera tubo desagüe lavadora y Manguera conexión toma de agua lavadora. Goma para empalme de vaciado de lavadora a desagüe y Goma para conectar lavadora a grifo : Amazon.es: Grandes

GOMA DE LAVADORA (Como empalmar la GOMA de ENTRADA y SALIDA de agua). 2020.#CURSO DE FONTANERIA - YouTube

BricoLoco Manguera conexión agua lavadora. Goma para conectar lavadora a grifo. Tubo toma de entrada de agua. Con un racor recto y otro curvo. Tuercas de 3/4". (200) : Amazon.es: Grandes electrodomésticos